| Uploader: | Fenrisar |
| Date Added: | 2 March 2005 |
| File Size: | 20.36 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 17565 |
| Price: | Free* [*Free Regsitration Required] |
ADefault parameter defines the default value in the field.

The most typical user-mode Rootkits Hacker Defender particularly may be blocked in this way. Suspends scanning after each file for the defined time period.
The Pause button enables you to pause scanning. The Cookies Found tab enables you to view the cookies containing the defined pattern and view the whole content of the file View Text button. About gHacks Ghacks is a technology news blog that was founded in by Martin Brinkmann.
My antivirus monitor reports avz*.tmp as an infected file or malware during scanning
Search for modifications at the disk of the protected computer. Blocking kernel hooks, rebooting the system, modifying SPI settings and Autorun items, etc. Filtering enables you to choose the certain type of items to be represented in the table of monktoring Services By API Data tab. Please use the System Recovery scripts to repair the settings. The Options tab contains the settings of the comparison.
Solvusoft: Microsoft Gold Certified Company
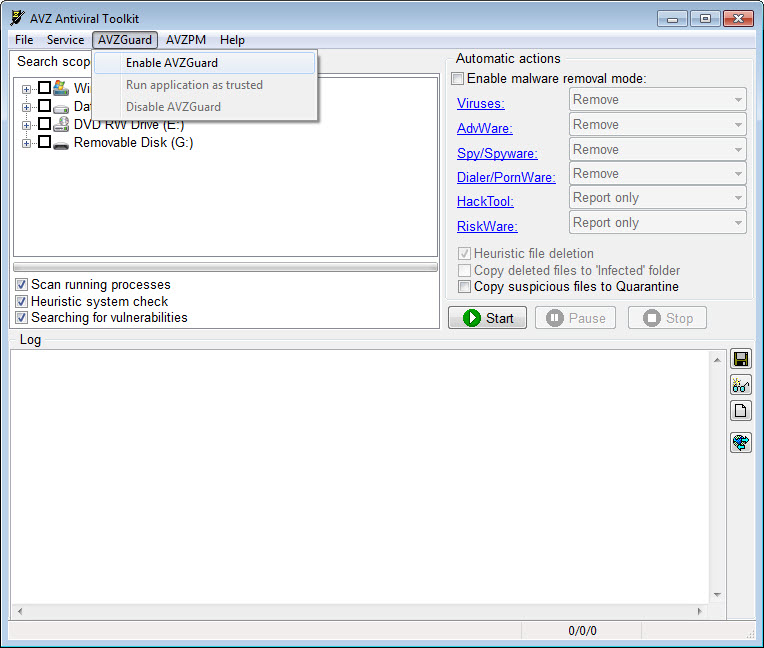
It contains all information required to perform the comparison. You select the drives that you want to scan here, whether you want to include a scan of running processes, use the heuristic system check, and search for vulnerabilities. The log may be copy-pasted or saved to a text file using the corresponding button.
If you try to enable AVZPM if it has already been activated, or to disable it if it is not active, no action will be performed.
That means that the information transferred does not contain any crucial data like passwords, credit card numbers, etc; as a rule, the downloaded data are ads or updates.
Kaspersky's AVZ Antiviral Toolkit is a portable second-opinion scanner - gHacks Tech News
This check is performed at Maximum heuristics level only. Backup procedures are stored in AVZ database and thus can be updated. This information is used in marketing and target advertisement. Procedure SetupAVZ can be used several times within the limits of one script; every call of the procedure modifies one parameter.
Kaspersky's AVZ Antiviral Toolkit is a portable second-opinion scanner
When the type is selected, choose the dangerousness level of the issues to be searched for. What to monitorinf when AVZ detects a suspected virus or malware?

In this mode you should also input login and password. The Inspector is protected by Anti-Rootkit subsystem. Neither AVZ window nor tray icon are displayed.
The file list should be inputted in the File List field, one line for each path. This option will enumerate privacy-related objects that exist in your operating system temporary files, cookies, browser cache and history, all sorts of logfiles and many more and let you clear or remove them. Monitorign threshold may be defined by the user, but it cannot be less than 1 Mb. Partially this problem may be solved using a heuristic analyzer — a special subsystem capable of detecting new viruses not described in the signature database by their characteristic features.
The only exception is the database update launched by the user. If you choose to save the files to an already existing ZIP archive, the files are added to this archive.
While I make sure that I run only programs that do not cause stability or compatibility issues when they run at the same time, I also run second-opinion scanners regularly to get a third, fourth or fifth opinion on the security state of the PC.
Also a Rootkit may hide some processes, files, folders, registry keys — if they are described in its configuration. No cache is used: The Heuristic Engine scans the registry, disk files, processes and libraries in the memory, active services and drivers, checks open ports in the system. ARepParams — the bit mask, defining logfile configuration.

Comments
Post a Comment